Services
Cybersecurity Assessments
Risk-based technical assessments, focusing on vulnerability exploitation impact and relying on three main cyber security factors: technology, people and processes.
Certified penetration testers and security analysts are the core of our cybersecurity assessment team. Following an ethical hacker's mindset, we provide you with clear visibility on your organization's strong and weak areas and mitigation pathways to reduce risk and maximize your security posture.

ISO Compliance & Consulting
Compliance with standards has always been a cornerstone for organizational and enterprise security. Taking into consideration the current demanding security environment, SpearIT offers you complete compliance services against well-known and security and trust services standards.
PCI Compliance
Complete PCI ASV (Approved Scanning Vendor) and QSA (Qualified Security Assessor) services covering every PCI standard and compliance level for merchants and payment service providers.


eIDAS Compliance
A team of qualified and expertised eIDAS subject-matter experts, providing full-fledged compliance and consutling services on the requirements of the Regulation and applicable standards, with subsequent conformity assessment services, enabling certified business activity within the European Digital Signle Market.
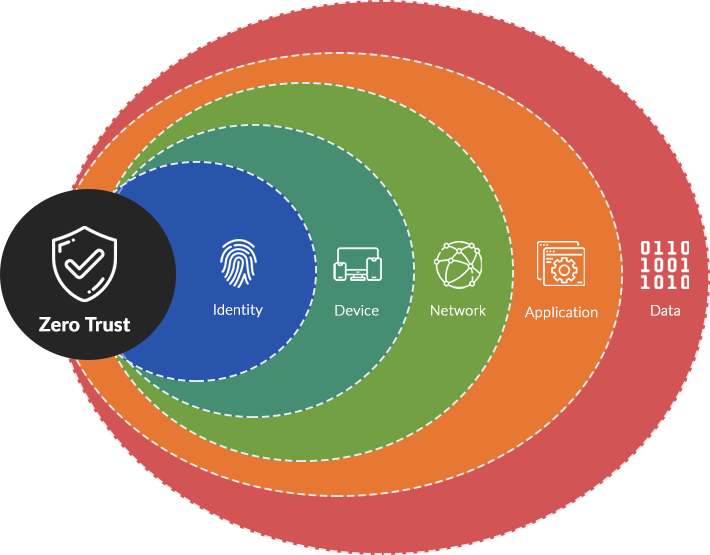
Zero Trust Consulting
Transform your traditional perimetric seucirty model to a dynamic and adaptive, never trusting-always verifying architecture, reducing your organization's attack surface and preventing lateral movement.
CISOaaS
A holistic approach on cyberecurity consulting and compliance. A multidisciplinary team of certified cybersecurity professionals ready to drive your organization's security program under the "as a Service" model.
GEIT Consulting
Governance of Enterprise Information and Technology (abrv. GEIT) is an activity which allows stakeholders to engage in setting direction and monitoring performance against enterprise objectives while addressing the complex regulatory environment of various industries and jurisdictions as well, by designing, implementing and sustaining a governance system.


Key Attestation
By leveraging our team of accredited PKI auditors, you receive a signed attestation letter regarding the proper generation of code signing & document signing key material inside FIPS 140-2 Level 2 or Level 3 compliant devices of major vendors and cloud service providers.
Secure SCRUM
Utilizing our Secure SCRUM coaches, your organization manages to proactively address security concerns during your agile software development lifecycle, reducing attack exposure and maximizing ROSI.

Latest News


Cypriot National eID becomes notified
